|
ERCIM News No.49, April 2002
|
Towards Digital Credentials
by Stefan Brands
Digital Credentials are the digital equivalent of paper documents and other tangible objects traditionally used for establishing a person's privileges, characteristics, identity, and so on. Since they are just cryptographically protected binary strings, they can be electronically transferred and can be verified with 100 percent accuracy by computers. Digital Credentials preserve the key privacy properties of paper-based documents and plastic tokens, but offer much greater security. They are entirely feasible, as R&D work during the 1990s has shown. Several academic prototypes have been developed recently, and a new Canadian company, Credentica, is now commercializing Digital Credentials.
Often at least one of the parties in a transaction needs to know whether the other party is authorized to perform a certain action. Typically, authorization is granted on the basis of a person's privileges, personal characteristics, reputation, identity, membership to a group, willingness to provide value in exchange, and so on. In all these cases, the verifying party must rely on the inspection of one or more tangible objects issued by trusted third parties. Examples of such 'credentials' are coins and bank notes, stamps, medical prescriptions, cinema tickets, voting ballots, membership cards, access tokens, diplomas, passports, and drivers' licenses.
Physical credentials are increasingly prone to counterfeiting, however, and cannot be transferred by mobile devices, personal computers, and chipcards. Well-known cryptographic techniques, such as digital identity certificates and message authentication codes, are not a solution:
- they encourage large-scale identity fraud and other devastating abuses of security holes that are inevitably caused by fundamentally relying on the central storage and management of sensitive information
- they ignore the privacy rights of individuals: all their actions can be linked and traced automatically and instantaneously, by a multitude of parties
- they do nothing to discourage participants from using each other's credentials.
To overcome these fundamental drawbacks, a transition to cryptographically protected digital forms of credentials is inevitable. (See S. Brands: "Rethinking Public Key Infrastructures and Digital Certificates; Building in Privacy," with a foreword by Ronald L. Rivest. August 2000, MIT Press, ISBN 0-262-02491-8, http://www.credentica.com/technology/book.html; and "A Technical Introduction To Digital Credentials," International Journal on Information Security, ed. Moti Yung, to appear in the August 2002 issue, http://www.credentica.com/ technology/overview.pdf.) It is entirely feasible to design Digital Credentials that address the complete spectrum of security, liability, and privacy risks for all parties involved. Digital Credentials preserve the key privacy properties of paper-based documents and plastic tokens, but offer much greater security and functionality:
- they are just sequences of zeros and ones, and so they can be transferred electronically and can be verified with 100 percent accuracy by computers
- the holder of a Digital Credential can selectively disclose a property of the data that the issuer encoded into it, without revealing anything else. For example, the holder of a 'privacy-enhanced' national ID card can prove that her Digital Credential specifies an identity that is NOT equal to one of several identities on a list of criminal suspects, without revealing her identity
- lending of a Digital Credential can be discouraged by encoding confidential data into it, such as a credit card number of the applicant. Even though the applicant can hide the confidential data when using the Digital Credential himself, it is not possible to use the digital credential without actually knowing the confidential data
- a limited-show Digital Credential can contain a built-in identifier that can be uncovered by a central party only if the Digital Credential is shown more than a predetermined number of times. See the Figure for an example. This property can be used to design secure electronic coins, stamps, gift certificates, and other value tokens
- they can be issued to, or embedded in, low-cost chipcards or other tamper-resistant devices. This provides an additional layer of protection against loss, theft, extortion, lending, copying, and discarding of digital credentials, and can prevent other kinds of unauthorized behaviour.
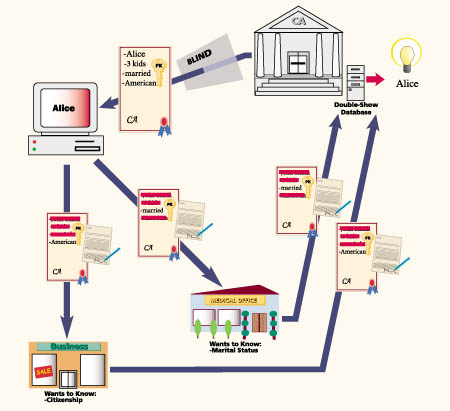 |
Alice fraudulently uses the same one-show Digital Credential at both a medical office and a business. Although each separate transaction cannot be traced by anyone to her identity, the aggregate information is sufficient to enable the central authority to find out her identity. |
Digital Credentials are suitable for any communication or transaction system that needs to protect the transfer and storage of information. Examples are access control systems (for VPNs, subscription-based services, Web sites, databases, buildings, and so on); privacy-enhanced national ID cards; public transport tickets; electronic voting; e-health systems; financial securities trading; digital copyright protection; road-toll pricing; and electronic money.
The practicality of Digital Credentials has been well-established. Notably, last year Zeroknowledge Systems in Montreal developed a wireless prototype for RIM's Blackberry as well as a software development toolkit suitable for a wide variety of applications. Also, from 1993 until 1999, CAFE and OPERA, two major European consortiums co-funded by the European ESPRIT Programme, implemented and extensively tested a chipcard-based electronic cash system based on the Digital Credentials technology. (See Rafael Hirschfeld: "OPERA - Open Payments European Research Association", ERCIM News no.30, July 1997, http://www.ercim.eu/publication/Ercim_News/enw30/hirschfeld.html.) Furthermore, several computer science graduates in Europe and America have independently developed academic prototypes.
In January 2002, a new company called Credentica was founded to commercialize Digital Credentials. Incorporated in Quebec, Credentica's mission is to deliver multi-party secure solutions for applications that involve the electronic transfer of sensitive information. Credentica leverages the Digital Credentials technology and its specialized R&D expertise to develop tailored software and services for the providers of Internet, wireless, and chipcard applications.
Link:
Credentica: http://www.credentica.com
Please contact:
Stefan Brands, McGill University,
School of Computer Science, Canada
Tel: +1 514 985 4111
E-mail: brands@credentica.com
